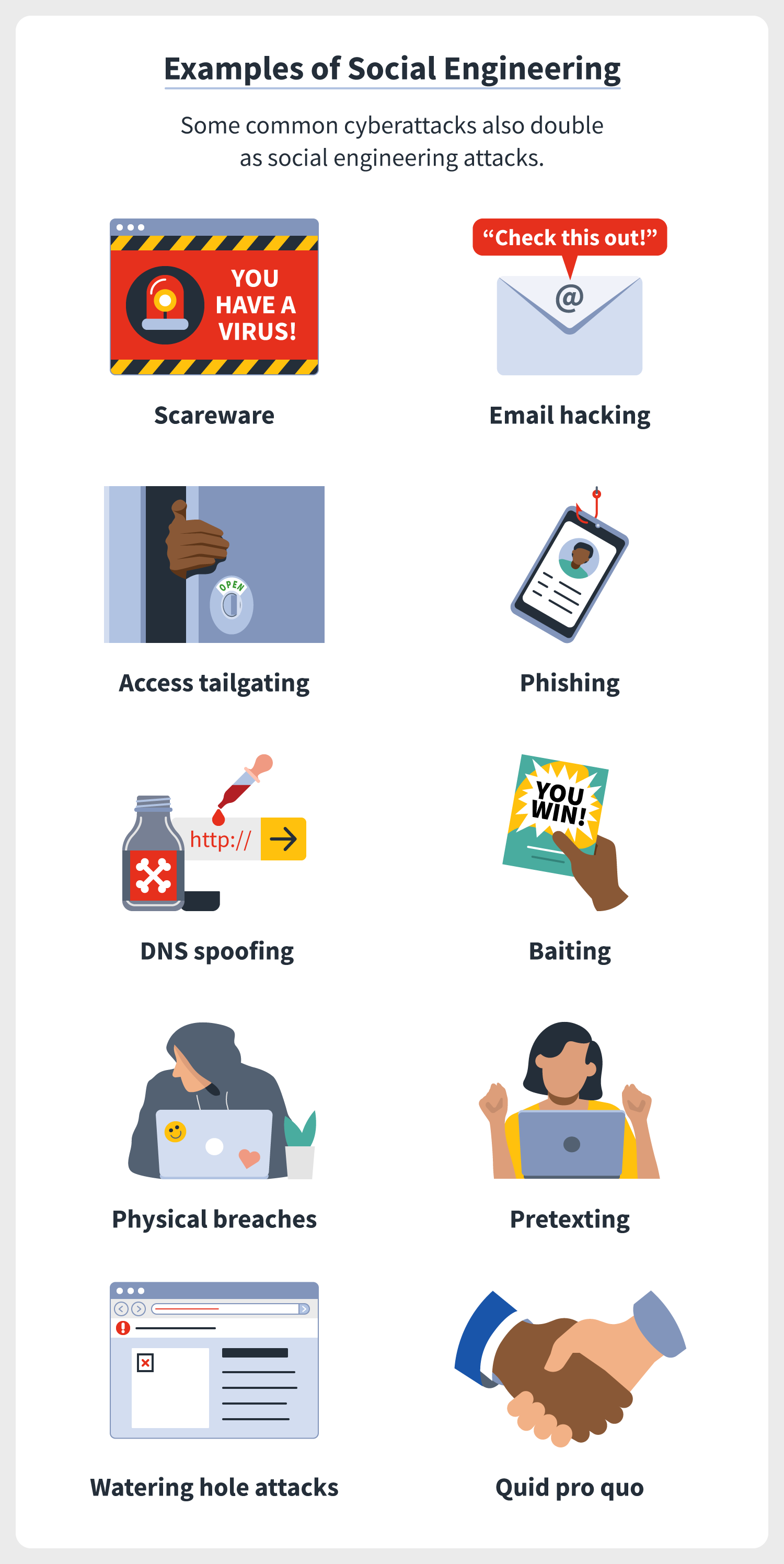
What is Social Engineering?
How social engineering works
Like most types of manipulation, social engineering is built on trust first— false trust, that is — and persuasion second. Generally, there are four steps to a successful social engineering attack:
- Preparation: The social engineer gathers information about their victims, including where they can access them, such as on social media, email, text message, etc.
- Infiltration: The social engineer approaches their victims, usually impersonating a trustworthy source and using the information gathered about the victim to validate themselves.
- Exploitation: The social engineer uses persuasion to request information from their victim, such as account logins, payment methods, contact information, etc., that they can use to commit their cyberattack.
- Disengagement: The social engineer stops communication with their victim, commits their attack, and swiftly departs.
Depending on the social engineering attack type, these steps could span a matter of hours to a matter of months. No matter the time frame, knowing the signs of a social engineering attack can help you spot — and stop — one fast.
Signs of a social engineering attack
Social engineering can happen everywhere, online and offline. And unlike traditional cyberattacks, whereby cybercriminals are stealthy and want to go unnoticed, social engineers are often communicating with us in plain sight. Consider these common social engineering tactics that one might be right under your nose.
Your “friend” sends you a strange message
Social engineers can pose as trusted individuals in your life, including a friend, boss, coworker, even a banking institution, and send you conspicuous messages containing malicious links or downloads. Just remember, you know your friends best — and if they send you something unusual, ask them about it.
Your emotions are heightened
The more irritable we are, the more likely we are to put our guard down. Social engineers are great at stirring up our emotions like fear, excitement, curiosity, anger, guilt, or sadness. In your online interactions, consider the cause of these emotional triggers before acting on them.
The request is urgent
Social engineers don’t want you to think twice about their tactics. That’s why many social engineering attacks involve some type of urgency, such as a sweepstake you have to enter now or a cybersecurity software you need to download to wipe a virus off of your computer.
The offer feels too good to be true
Ever receive news that you didn’t ask for? Even good news like, say winning the lottery or a free cruise? Chances are that if the offer seems too good to be true, it’s just that — and potentially a social engineering attack.
You’re receiving help you didn’t ask for
Social engineers might reach out under the guise of a company providing help for a problem you have, similar to a tech support scam. And considering you might not be an expert in their line of work, you might believe they’re who they say they are and provide them access to your device or accounts.
The sender can’t prove their identity
If you raise any suspicions with a potential social engineer and they’re unable to prove their identity — perhaps they won’t do a video call with you, for instance — chances are they’re not to be trusted.
Email Social Engineering
Ever get an email message from your bank warning you that your savings and checking accounts have been locked because of suspicious withdrawals? That email might ask you to click on a link embedded in the message to verify your identity and keep your account open.
Don’t fall for this scam. The odds are that the email is an example of phishing, an attempt by scammers to trick you into providing personal or financial information that they can then use to steal money from your bank accounts, make fraudulent purchases with your credit cards, or take out loans in your name.
If you do click on a link in a phishing email, you’ll usually be taken to a new web page that looks like it belongs to your bank or credit card company or even PayPal. That page will ask you for your personal and financial information — maybe your account numbers or log in credentials, like your username and password. Once the scammer behind this bogus page gets that sensitive information, they can easily access your financial accounts.
Phishing is a form of social engineering — phishers pose as a trusted organization to trick you into providing information. Phishing attacks are showing no signs of slowing. But if you’re careful, you can avoid falling victim to them. Remember, your bank or credit card provider will never ask you to provide account information online. When emails ask for this information, that’s the first sign that they’re scams.
Check the links that these emails ask you to click, too. If you hover over them, you’ll see their true addresses. They’re usually not affiliated with the bank or credit card provider they are spoofing.
Fortunately, there are usually other telltale signs that an email is phishing for your personal information. Below are examples of recent phishing emails. We’ve analyzed these emails so you’ll know what to look for when determining whether an email is legitimate or a scam. And that can help you boost your cybersecurity.
Recognizing phishing email scams
What are some general clues that an email isn’t legitimate but is instead a phishing email?
Grammatical errors
Many phishing emails are filled with grammatical errors, odd capitalization, and misspellings. The emails might also contain odd phrases or sentences that sound a bit off. Read your email aloud. If something doesn’t sound right, or professional, be suspicious. It could be a phishing attack.
Low-resolution logo
Phishers will often cut and paste the logos of government agencies, banks and credit card providers in their phishing emails. If the logo is of low quality — it’s fuzzy, indistinct, or tiny — this is a sign that the person contacting you doesn’t really work for that company.
Odd URL
One of the easiest ways to tell if an email is a scam? Hover over whatever link the message is asking you to click. This will show the link’s URL. Often, you’ll see that the URL doesn’t belong to whatever company is supposedly sending you the message.
Again, this is a sign that a scammer is trying to trick you. Just be careful when hovering. You don’t want to accidentally click on the link.
Here are some phishing examples to consider.
Phishing email example: Instagram two-factor authentication scam
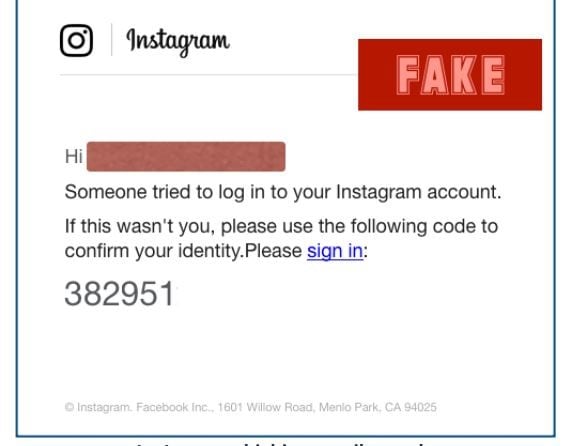
Two-factor authentication, or 2FA, is one of the best ways to protect your personal or financial information. When you log onto a site — say your online bank or credit card provider — you’ll have to provide your username and password as usual. If you have two-factor authentication enabled, the site will then send a text or email to you with a code. You must enter that code before you can complete your log in to the site.
Scammers, though, are now using this extra security measure as a way to trick you. A new phishing campaign is targeting Instagram users, sending them emails claiming that someone has tried to log into their Instagram accounts.
The email asks recipients to sign into a site that is supposedly run by Instagram, a social media service. It’s not, of course. But what’s interesting is that the scammers include a code at the bottom of the message, implying that users should type that code in — as if it was an example of two-factor authentication — when they sign into the spoofed web page.
How can you tell it’s fake?
This is a well-done scam. There is one tell-tale sign that the email is fake, though. If you click on the link and access the spoofed website, the domain name displayed in your browser’s address bar will be .CF. That is a country code for the Central African Republic. That’s why it’s smart not to click. Instead, hover over the link to see the true address.
Phishing email example: Account temporarily suspended

You might receive a notice from your bank — or another bank that you don’t even do business with — stating that your account has been temporarily suspended. Why? According to the email, your bank has discovered unusual activity on your account and has decided to shut it down to protect you.
The email will then ask you to click on a link to reactivate your account. This link will take you to a fake page that asks for your user ID and password.
This, of course, is fake. When you enter your account information, you’ll be giving it directly to a scammer.
How can you tell it’s fake?
There are usually several clues that such emails are fake. First, look for spelling or grammatical errors. In the example above, supposedly sent by SunTrust, you’ll see that the sentence “We recently contacted you after noticing on your online account, which is been accessed unusually” doesn’t really make any sense.
If you hovered over the Suntrust.com link in the live version of the image above, you’d see a link to a shortened URL at bit.ly. If you unshorten that link, you’ll discover that it leads to a pet-food company in Israel, not to SunTrust.
Phishing email example: Tax refund scam

Getting an unexpected windfall of cash? Who wouldn’t want that? Be careful, though: If someone sends you an email saying that you’re due a refund or cash prize of some sort, it’s usually a scam. Consider a common version of this, the IRS refund phishing attempt.
You might receive an email that looks like it comes from the IRS. The headline will promise that you are owed a refund from the agency and that you can claim it online. The body of the message will usually state that the IRS made an error in calculating your tax bill, and now owes you money, maybe hundreds of dollars.
When you click on the link included in the email to claim the alleged refund, you’ll either run into a spoof site designed to trick you into giving up personal and financial information or your computer or device could be exposed to malware.
How can you tell it’s fake?
There are clues to alert you that this message is fake. The biggest, though, is the message itself. The IRS will never email you to ask for your personal information. If you get a message saying that the IRS owes you money, call the government agency yourself to check. The odds are high that the IRS doesn’t owe you anything and that a scammer sent you the message.
Phishing email example: Netflix phishing scam
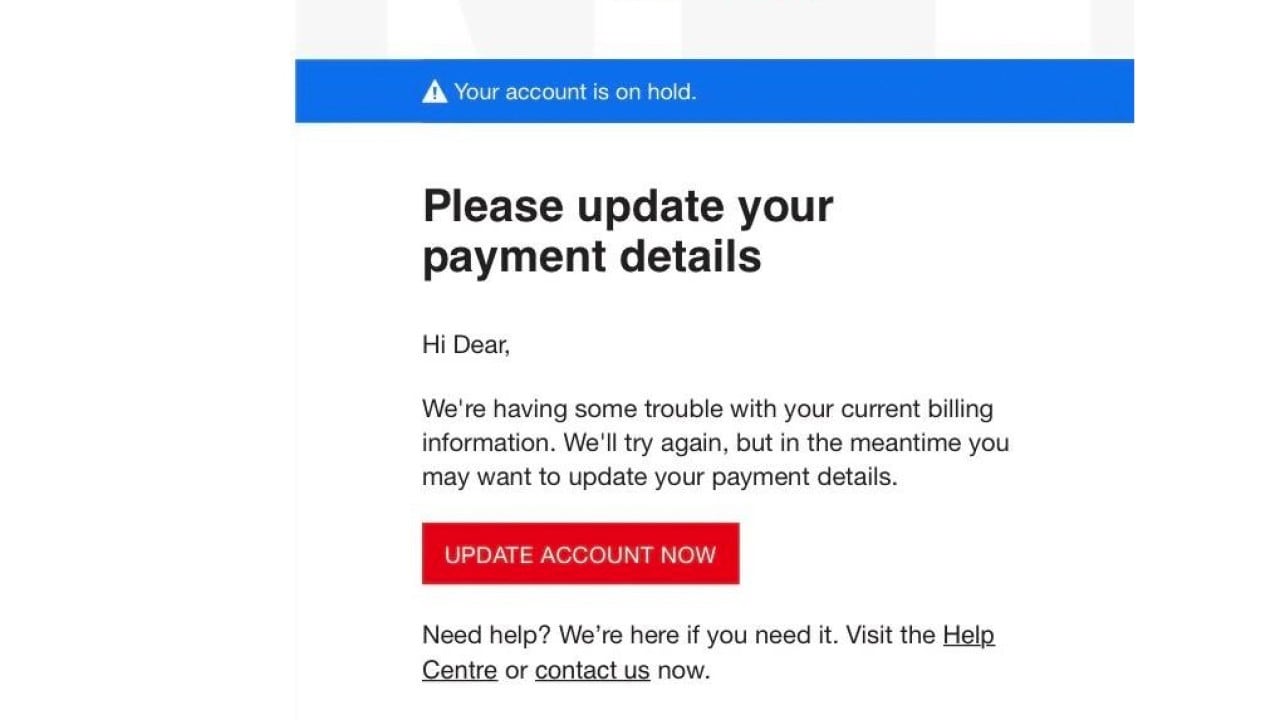
You never want your Netflix account to go down. But don’t worry about that email claiming your Netflix account is on hold. It’s a fake.
The Netflix account-on-hold scam is a popular one, probably because so many of us rely so heavily on Netflix for entertainment today. In this scam, criminals send an email, supposedly from Netflix, complete with the company’s logo, saying that the company is having trouble with your current billing information. You’re then asked to click on a link to update your payment method.
You know the rest: The link is a spoof site. When you enter your credit card information, you’re sending it directly to cybercriminals.
How can you tell it’s fake?
Again, Netflix won’t reach out to you through email to request your personal information. If you receive a message like this from Netflix, call the company directly to determine if you really do need to update your account.
Also, pay attention to the language of emails like this. In this example, the scammers behind the email start their message with the salutation "Hi Dear." No business would address its customers in that way.
Phishing email example: CEO phishing scam
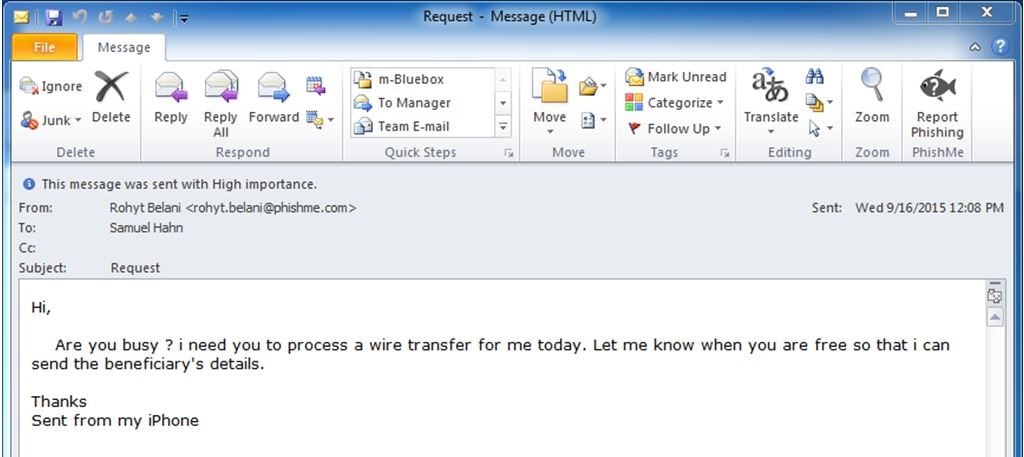
Some phishing attempts have limited targets but the potential for big paydays for crooks. A good example? The CEO phishing attempt.
Scammers send these emails to the employees of specific companies. The trick is that these messages come from addresses that appear to belong to the chief executive officer, chief financial officer, or other highly-placed executive in a company. The email will ask the employee to wire money — often thousands of dollars — to a vendor or client. Only later does the employee realize that the message was a scam.
How can you tell it’s fake?
CEO phishing emails are often sophisticated. You can look for misspellings or grammatical errors, but you might not spot any. You can check the email address of the sender, too. Often, it will be similar to the company’s email format, but with a slight difference.
The biggest clue, though, that these messages are fake? Wouldn’t your company’s CEO or CFO ask you in person to send large sums of money and not rely on sending such an important request through email?
If you do get one of these messages, no matter how legitimate it looks, contact the person who purportedly sent it. Make sure that the executive sent the email and that a savvy scammer isn’t trying to steal from your company.